Also provided by VirusTotal is a list of all the different filenames the malware has been submitted under. Selection of a system driver to replace is done using an internal algorithm. SEO Search Engine Optimisation techniques are used to drive compromised websites up search engine rankings, increasing the traffic that gets sent to the attack site. It appears that free videos and apps names are used as the lure in this case. Also this can also be done on many hosting sites that provide a DNS lookup. 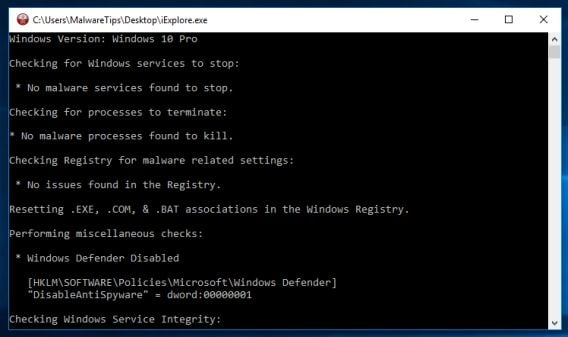
| Uploader: | Turan |
| Date Added: | 3 December 2010 |
| File Size: | 50.38 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 8897 |
| Price: | Free* [*Free Regsitration Required] |
tweemyym.tk
It is a very advanced rootkit that uses kernel calls and targets windows based machines. Traffic is driven to websites hosting exploit packs through a variety of means. First, zeroaccss ACL of the file for the process that has opened the bait process is changed so that the file can no longer be executed, using ZwSetSecurityObject: Note You need administrative rights to change the settings.

Contact Support Chat with or call an expert for help. It is not a residence.
Before scanning, enable the product to scan system files by following these steps:. User Guide See the user guide for your product on the Help Center. The lure is often a piece of illicit roootkit such as a game or a copyright protection bypassing tool such as a crack or keygen.
This will most likely make browsing in Internet Explorer insecure. The analysis summary of the report from Annubis can be seen in Figure 1. These three services allow for web submission of the sample file. File System and Registry Behavior. Newer Post Older Post Home. Fill in your details below or click an icon to log in: Fill in your details below or click an icon to log in: It has also been reported as being distributed via compromised legitimate websites. The rootkit will display the contents of the original system driver, presumably to camouflage its presence on the system.
Dropper ZeroAccess droppers have changed as the rootkit itself has evolved. It is residing in the recycle bin! We are able to see the registry keys and new values that are created for each element.
The bot also listens on the same high numbered TCP port that outgoing connections use, thus it attempts to become another node in the peer-to-peer botnet.
Otherwise the infected machine will effectively become a passive node that can only connect to other nodes and obtain data; it cannot be connected to by other nodes. Ad servers have also been compromised in this way which can result in widespread infection very quickly if the ads are served to high profile websites.
Mario's Security Blog: ZeroAccess Rootkit - Part 1
Social engineering The second main infection vector for ZeroAccess is through a variety of social engineering techniques. First check if your F-Secure security program is using the latest detection database updates zeroaaccess, then try scanning the file again.
Panda Suspicious file It appears that free videos and apps names are used as the lure in this case. After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis. The packers contain a great many anti-emulation and anti-debug techniques designed to defeat emulators inside AV engines and to make analysis inside a controlled environment more difficult.
The ZeroAccess rootkit
Anonymous December 26, at 5: It is a proxy IP of the sandbox - if you go there, will probably find a large data center. The first is a type of click fraud malware that appears zeroaccesx be very tightly bound to ZeroAccess, so much so that it may have been authored by the ZeroAccess owners. You are zeoraccess using your Facebook account. I do have a sample, but need help to reverse some of the damage done! Submit a sample Submit a file or URL for further analysis.

No comments:
Post a Comment